On average, consumers are attacked within 71 seconds of landing on a piracy site, your identity and access credentials can be stolen, and you can be subjected to a ransom demand. RATs (Remote Access Trojans) in your devices are just the beginning.
This study examined malware infection techniques across a broad range of actors targeting European consumers, finding that malware can be downloaded through malicious advertising, malicious popups, fake browser extension installations, browser notification hijacking, blocking notifications, adware, malicious software installation and banner ads. Furthermore, the study found an average 57% chance of an audiovisual piracy app being installed with embedded malware.
While European policymakers have focused on strengthening cybersecurity protections for many years, an AAPA study released in September 2022 found that these protections have had little impact on the risk of malware delivered through audiovisual piracy.

Estimates vary as to the size of the risk to consumers
- A recent study from the Asia Video Industry Association (AVIA) suggested that consumers believe that 31% of malware infections could be attributed to visiting piracy sites, using piracy apps, or set top boxes (STBs) that provide pirated content. In a separate AVIA study, researchers found that serious malware infections typically occurred in less than one minute after the first visit to a site
- UK-based FACT highlighted the scale and significance of the problem in the UK. 50 streaming sites were analysed, with more than 90% being classified as risky by cybersecurity experts, with users being inundated with pop-ups, trojans, banking malware and other infections being observed. 40% of these sites had no security
What is malware?
We’ve all heard the term. The AAPA defines malware as “computer code that is installed and executes on any device – such as a PC, smartphone or Smart TV – with the purpose of compromising that device, by a malicious actor(s), which range in capacity and cyber security skill; from nation states (for intelligence) through to organised crime groups (for money), as well as amateurs (often for curiosity). They lure users with attractive offers, while infecting them with malware.
PC malware
The report identifies four sources of PC malware, three of which are associated with audiovisual piracy:
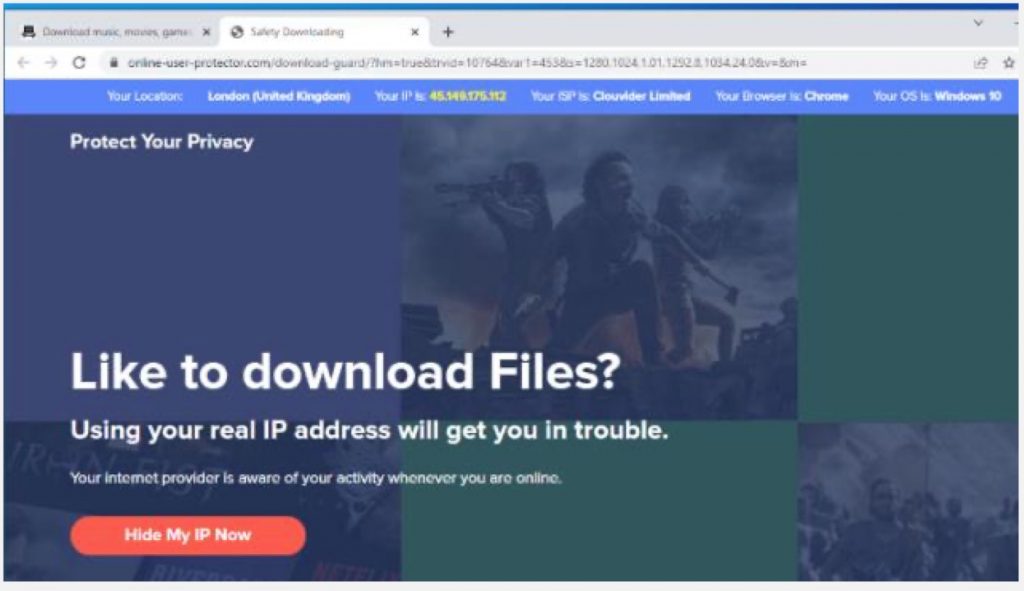
- “Shady” Websites – users are lured into downloading or installing seemingly legitimate software which is actually malicious, often disguised as games or software updates, and/or making promises of “free money”. Advertising on these sites is also often used as a malware download vector;
- P2P File Sharing – users install P2P client software that can be used to also download malware, or potentially participate turn consumer PCs into “bots” to support Denial of Service (DoS) attacks;
- Torrent Downloads – consumers may seek to download pirated content, including software which may have malware embedded, or key generators and software “cracks” may also contain malware;
- Phishing Emails – while they are not ‘audiovisual,’ some phishing emails contain embedded malware; when the attachment is downloaded, it can execute and immediately gather sensitive data about the user.
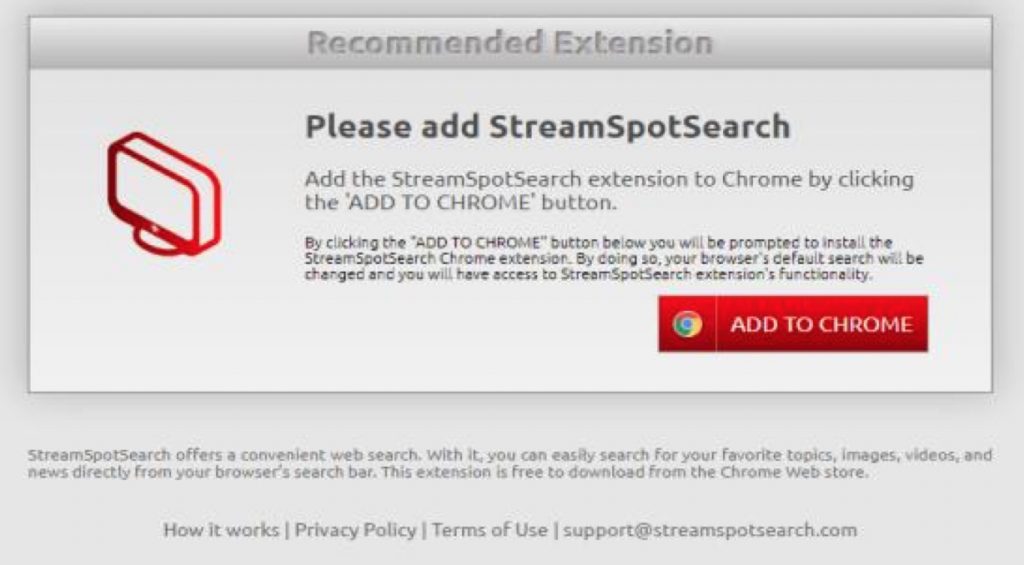
Consumers are attracted to install malware in several ways
- Pop-up windows. When a JavaScript event is triggered, such as clicking in a window, on a link or search box, a popup appears, which can be used to install malware through a third-party site. In turn, the installed malware can also popup new advertising banners, insert hyperlinks into plain text pages, recommend fake updates (potential malware) or install other third party applications.
-
CPC (Cost per Click) Fraud Malware, which is designed to generate advertising revenue for its authors by simulating clicking on ads on other sites, where the author is paid through a CPC Cost Per Click) scheme.
Browser Notification Hijacking. Notifications may contain web links to malware downloads; other times they can be used to display ads from legitimate advertisers, or fraudulent ads that appear legitimate and provide a path to download.
Browser Extension Installation. The user may be presented with a pop-up window that then triggers a request to install a browser extension, framed in such a way as to maximize compliance, for example, an extension may be required to view a stream or a video using a new CODEC. Invariably, these code extensions contain malware.
-
Adware. This form of malware replaces ads served up by an ad network embedded on a Web page by ads generated by a hijacker. The ad network loses revenue, and the hijacker gets revenue from its own ad.
Do you smell a RAT (Remote Access Trojan)?
Users can also be prompted to install Remote Access Trojans (RATs), which are installed by users expecting to receive technical support and allowing a fraudster to install software to help them through a technical support incident, say, by screen-sharing. But the actual software is malware.
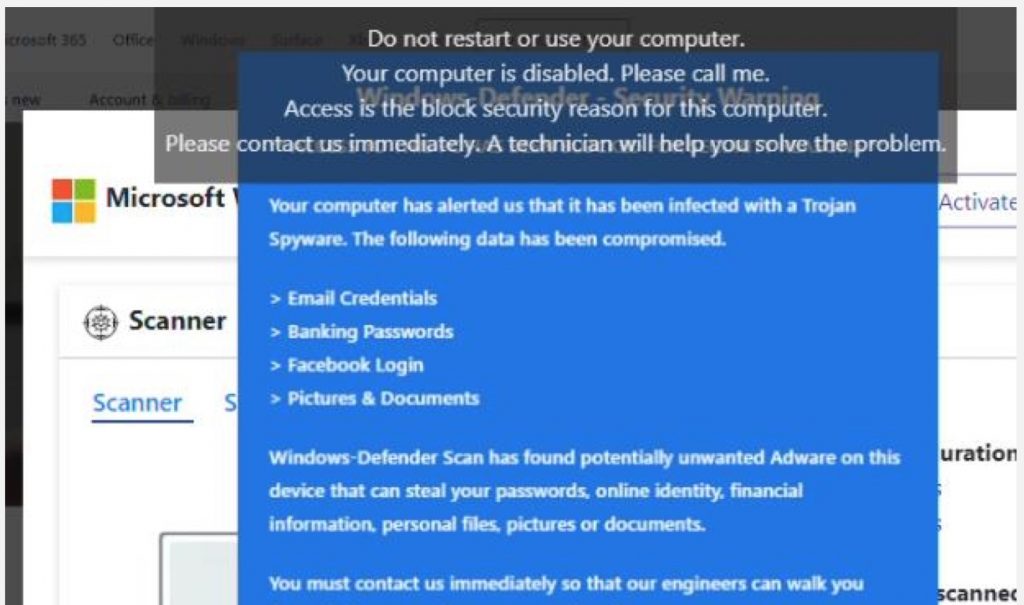
a variation on the technical support scam, where a Remote Access Trojan (RAT) is installed on a consumer’s PC (Source: AAPA) Malware via Mobile
The report also details malware delivered mobile devices, and found that the mean chance of downloading an IPTV app with embedded malware was 57% – more likely than not, with each app installed, users will be infected.
Malware is also delivered to mobile devices via banner and interstitial ads, and through subscriptions that required device registration (MAC address).
Malware via STB
As was the case for mobile, streaming set-tops targeted by malware were typically Android-based.
AAPA received reports of STBs being targeted by botnets to recruit them to participate in Distributed Denial of Service (DDoS) attacks. This may be because of their limited user interface and use of default superuser user accounts, providing full administrative access, especially where the STB or Smart TV has been “rooted”. There are comprehensive instructions on how to achieve this freely available on the internet. A compromised STB could provide a foothold for malware to then spread laterally within the local area network
Download and read the full report: Cyber Risk for European Consumers, The Rise of Malware (by AAPA)
Why it matters
AAPA notes that Europe has very strong cyber and privacy frameworks, such as the GDPR, ENISA, the INS Directive and the Cybersecurity Act. These include the development of digital identities which are cryptographically verifiable. Yet the downside of strong identity management is the risk that these digital wallets can be taken over by malware installed from audiovisual piracy sites. It is worrying that malware does not even appear to have been considered in the design of the European Digital Identity Framework, opines AAPA.
One estimate cited in the report holds that 1% of all adds served globally are injected with malware. The impact to consumers includes identify theft, credential theft, or ransom demands, leading to identity fraud, cyberfraud and extortion.
Malware can infiltrate businesses when a consumer connects to a corporate network while viewing an audiovisual piracy site, or using an audiovisual piracy app, and then move laterally within a corporate network. Corporate backend systems could be ransomed, costing business potentially many millions of dollars in ransom being paid, or large parts of the business could become unable to operate due to data loss. Or, malware could be installed using this path, in order to monitor all corporate network traffic, and exfiltrate this data to a malicious third party for espionage purposes.













