Experts in the Field
Contributed articles about piracy and anti-piracy, by respected experts in the media and entertainment industry and by those who serve them.
See Blog for articles and opinions of Piracy Monitor.
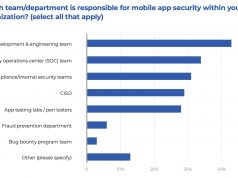
Enterprise security pros say their own apps are secure. Third party apps not so...
A fall 2023 survey of 100-plus cybersecurity professionals conducted by Information Security Media Group explains how compromised mobile apps can expose enterprise servers, back-end...
Stopping piracy before it starts: TPN’s Terri Davies interviewed by The Bulwark
This post links to an interview of Terri Davies, President of The Trusted Partner Network (TPN), by Sunny Bunch, reporter for The Bulwark.
TPN is...
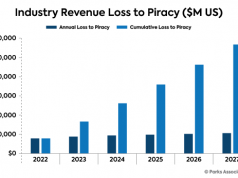
Parks: Cumulative US streaming revenue lost to piracy may exceed $113 Billion by 2027...
The comprehensive report addresses piracy for streaming & digital media services and how to fight it.
At NAB this week, Parks Associates announced by the...
Thought Leadership: Five steps to a successful Anti-Piracy and Cybersecurity Management Program
By Mark Mulready - Vice President - Cyber Services at Irdeto
Cyber-attacks have become increasingly sophisticated and frequent and the need to manage cyber risks...
The bigger picture: Anti-piracy is an ecosystem that demands holistic thinking
“It’s difficult to put a dollar amount on piracy,” says Andrew Bunten, Chief Operating Officer of Video Entertainment at Irdeto. “But, there’s little mystery as to...
VSS 2022: Emerging piracy use-cases and anti-piracy countermeasures
We examine the the gap between content protection and anti-piracy and how a holistic approach can help close it. We also discuss how distributed...
VSS 2022: OTT Infrastructure Security – An End-to-End Proposition
As distribution has taken the ultimate leap to cloud-native infrastructures that serve multi-screen environments, OTT platform providers have placed a high priority on end-to-end...
VSS 2022: Pinpointing and Shutting Down Sports Piracy at Lightning Speed
Live sports content continues to be the most desirable for pirates to steal. Identifying infringing use is critical, both because the programming itself is...