In October 2021, the New South Wales (NSW) Supreme Court sentenced a 23-year-old Sydney man to a 2 year, 2 month intensive corrections order, and to forfeit AU$1.66 million following his conviction for selling illegally obtained logins for online services such as Netflix.
It culminated a five year joint investigation by the Australian Federal Police (AFP) and the US Federal Bureau of Investigation (FBI). The Australian had conspired with a US individual to steal the credentials of streaming service customers, selling credentials through 4 account-generator websites which had over 150,000 users.
More than $1.2 million of the proceeds were in cryptocurrency, making for the largest seizure of cryptocurrency in Australian history. Proceeds were money-laundered through a complex system of PayPal accounts and cryptocurrency wallets.
The initiative that took the operation out of service, called Operation Boone, was one of numerous cybersecurity case studies detailed in the third Annual Cyber Threat Report by the Australian Cyber Security Centre (ACSC), a key part of the Australian Signals Directorate (ASD).
Cybercrime trends
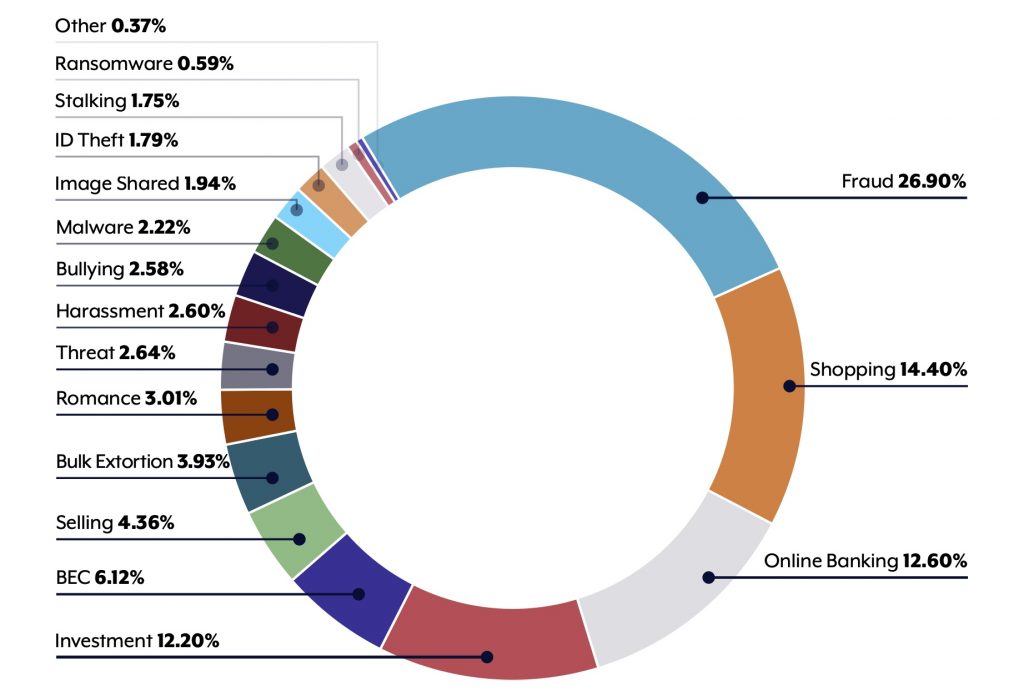
During the 2021-2022 study period, the ACSC observed that cyberspace is increasingly a domain of warfare by nation-state actors, targeting critical infrastructure that puts essential services at risk. Australia’s economic prosperity has attracted cybercrimes against individuals, compromising online banking, shopping and fraudulent business email. The report finds that ransomware continues to be the most destructive cybercrime.
Sweeping threat landscape
The report recognizes that cybersecurity incidents are committed by a variety of actors, including:
- State actors using cyber operations as a geostrategic tool to steal national secrets
- Cybercrime-as-a-service – which has become ncreasingly sophisticated and more accessible to ‘less technologically skilled’ actors. These include access brokering, hosting services, development obfuscation and distribution of malware, and phishing kit development.
- Business email compromise, to scam businesses out of money or goods. Cybercriminals also use it to pretend to be business representatives, send fraudulent invoices and to trick employees into revealing confidential business information
- Ransomware targeting, where the combination of data encryption and threats to publicly release sensitive information function as a method of pressuring ransomware victims into paying ‘double extortion.” Ransomware operators are “using third parties to negotiate with victims, assist them in receiving their ransom payments, and arbitrating disputes between actors.”
- Threats to critical infrastructure, which encompasses physical facilities, communication networks, and information and operational technologies that provide essential services. A sustained disruption in one part of the critical infrastructure ecosystem has knock-on effects elsewhere in the economy, and could ultimately lead to harm or loss of life
Over 2021–22, there were examples of ransomware groups targeting government and critical infrastructure organisations, as well as the finance and construction sectors globally.
Critical vulnerabilities
During 2021–22, the number of software vulnerabilities recorded worldwide increased by more than 25 per cent compared to the previous financial year. Over 24,000 Common Vulnerabilities and Exposures (CVEs) were identified.
Malicious actors conduct scanning and reconnaissance against internet-accessible networks to identify unpatched software. In some instances, cyber actors successfully compromised Australian networks using publicly disclosed critical vulnerabilities.
The rapid use of newly released critical vulnerabilities is now standard tradecraft for many malicious actors. Certain software and hardware is used ubiquitously across government, critical infrastructure, small business and by individual users, presenting malicious actors with a plethora of potential victim networks
What Australia is doing about it
The Australian government has made cyberdefense a national priority and urges individuals to make it a priority themselves. The ACSC launched a Cyber Threat Intelligence Sharing platform, and the government has invested in a strategic initiative to further harden the country’s cyber defenses, called REDSPICE (Resilience, Effects, Defence, SPace, Intelligence, Cyber, Enablers).
The ACSC urges cybersecurity stakeholders to follow its Strategies to Mitigate Cyber Security Incidents, to help organisations protect themselves against various cyber threats. One of its most effective mitigation strategies is designed to protect Microsoft Windows-based internet-connected networks: the Essential Eight Maturity Model. First published in June 2017 and updated regularly, it is based on the ACSC’s experience in producing cyber threat intelligence, responding to cyber security incidents, and its own penetration testing.
What the ACSC did
Among its accomplishments, the Austalian Cyber Security Centre:
- Blocked over 24 million malicious domain requests
through the Australian Protective Domain Name System. - Took down over 29,000 brute force attacks against Australian servers through the Domain Takedown Service.
- Took down over 15,000 domains hosting malicious software
targeting Australia’s COVID-19 vaccine rollout. - Collaborated with partners on 5 successful operations against criminal online marketplaces and foreign scam networks
- Led 24 cyber security exercises involving over 280 organisations to strengthen Australia’s cyber resilience.
About the report
Released in November 2022, the report maps how threat actors across the world have continued to find innovative ways to deploy online attacks, with supply chains used to penetrate cyber defences
of governments and organisations in many countries, including Australia.
Contributors to the Annual Cyber Threat Report 2021–22 include the Australian Federal Police, the Australian Criminal Intelligence Commission, the Australian Security Intelligence Organisation, Defence Intelligence Organisation and the Department of Home Affairs.
Download the report: July 2021 – June 2022 Annual Cyber Threat Report, by the Australian Cyber Security Centre, Australian Signals Directorate of the Australian Government.
Why it matters
“We are currently witnessing deteriorating strategic circumstances in our region and globally, including a military build-up unseen since World War II, and expanding cyber and grey zone capabilities are of particular concern,” said the Hon Richard Marles, MP, Deputy Prime Minister and Minister for Defence. “












