The informative paper explains stages of the live streaming process and the intermediaries involved, as well as ways that pirates evade and undermine anti-piracy efforts. It also explains advantages and limits of anti-piracy measures that can be implemented across the media ecosystem. It describes challenges to the parties involved and idenfies practices for dealing with the threats.
It also describes the most recent developments at EU Member States level to counter live event piracy, mainly consisting of getting national Internet Access Providers (IAPs) to promptly block access to illegal websites or streaming servers.
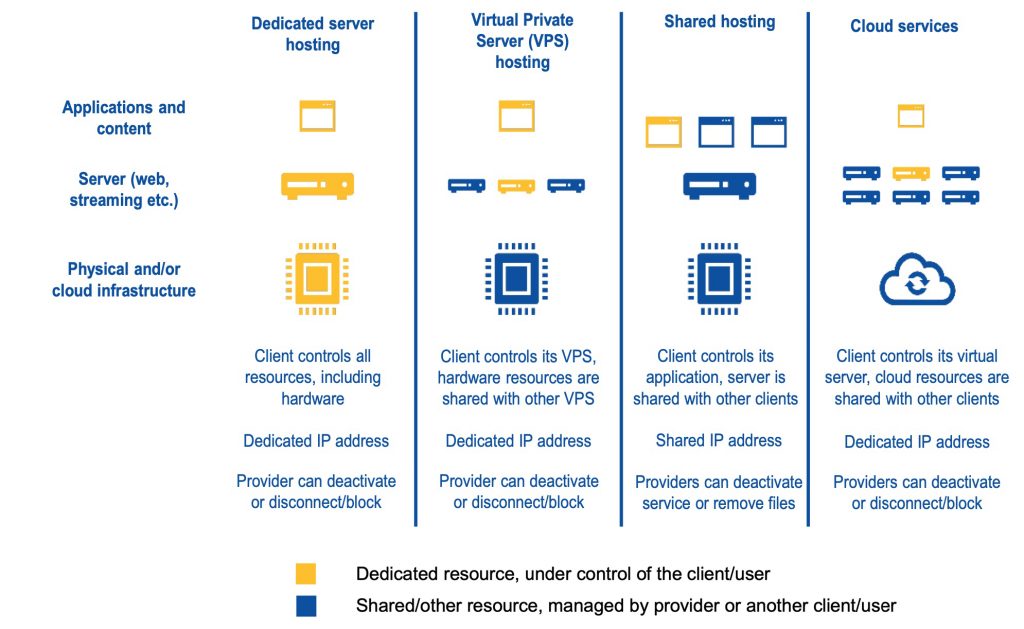
Another focus is on the technical intermediaries that are positioned more upstream in the live content streaming process, in particular Dedicated Server Providers (DSPs) and Content Delivery Networks (CDNs).
Streaming delivery
Four online distribution methods are illustrated in the EUIPO paper. Pirates endeavor to distribute stolen content in ways that enable them to reduce their exposure to detection.
Streaming and event piracy ecosystems
The report presents a mapping of the live event streaming ecosystem; including content generation and management, distribution and transmission, and content consumption.
It provides a current view of three prevalent live event piracy models: subscription-based IPTV, open IPTV streams and open Web streaming.
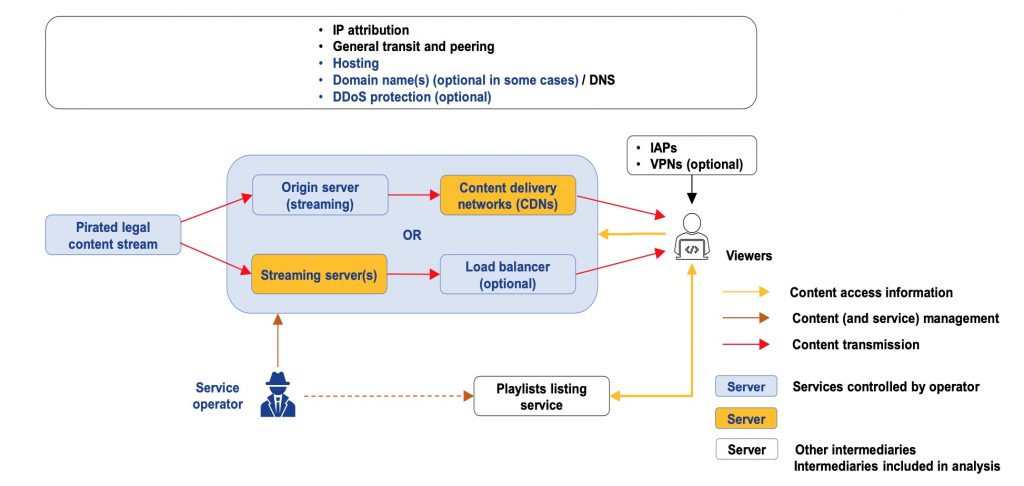
“IPTV” is defined as the presentation of unlicensed live TV channels and on-demand programming that includes live events through Web sites, media players and mobile apps; aggregated into a single user experience.
How pirates hide from anti-piracy
The report notes that piracy services implement resilience strategies to withstand or immediately recover from enforcement measures targeting their services. Typical strategies consist of setting up ‘mirror websites’ where their services can be reached under different domain names, or ‘fallback IT infrastructure’ where their services can be reached under a different IP address.
Live event piracy operators also make use of offshore hosting providers that are registered in countries with a lenient regulation regarding their activities, but use ‘onshore’ technical infrastructure to optimise content delivery. In recent years there has also been a development of Piracy as a Service (PaaS), which lowers the entry barriers to set up, operate and monetise piracy services and support live streaming of content.
Practices against IPTV piracy
Putting enforcement measures in place can be challenging. Countermeasures against piracy involve reconciling the need to quickly limit economic losses while preventing wrongful or overblocking to preserve the rights of third parties.
Good practices identified in the paper include live blocking injunctions against domains (DNS) or streaming servers (IP blocking) for the duration of an event. ISPs should also regularly add illegal services to blocking lists upon requests by rights holders. Several countries have adopted practices to obligate ISPs to end live event piracy, which are described in the paper. Others also adopt voluntary processes.
Cooperation against piracy
The paper builds on contributions of the EUIPO Observatory’s Expert Group on Cooperation with Intermediaries. It is intended to serve as a basis for discussion, particularly in view of the upcoming recommendation by the European Commission on combating online piracy of lived content.
The paper recommends that Dedicated Server and CDN providers reserve the right to block illegal traffic and ask their customers to disclose their details. DSPs should collaborate with rights-holders to establish near-instant take-down processes.
Access the Discussion Paper: Fighting the piracy of live events: trends, challenges and good practices. Report. March 15, 2023. Europan Union Intellectual Property Office Observatory.
Why it matters
Illegal live streaming of such events exploits the value of their content and is particularly damaging to the sectors that produce and distribute it.
To limit the damage the illegal streams need to be identified quickly and ultimately blocked. This poses new challenges for rights holders, online intermediaries – whose services are misused for such illegal activities – as well as to law enforcement and judicial authorities.












