
Operation MEDUSA, a court-authorized operation to disrupt Uroburos (“Snake”), a global peer-to-peer network of computers that had been compromised by a Russian malware platform, was completed, said the US Justice Department. Snake’s targets include media organizations.
Russia’s operation, attributed to a unit within Russia’s Federal Security Service (FSB) and known as “Turla,” was used to steal documents from computers in more than 50 countries across across North America, South America, Europe, Africa, Asia, and Australia and Russia itself; including NATO member governments, journalists and others of interest. US agencies have observed interoperable Snake implants for Windows, MacOS, and Linux operating systems, and remarked that it was carefully designed and relatively free of bugs.
Russia was said to commence Snake’s development in 2003, with initial deployment in 2004. “For 20 years, the FSB has relied on the Snake malware to conduct cyberespionage against the United States and our allies – that ends today,” said Assistant Attorney General Matthew G. Olsen of the Justice Department’s National Security Division in a May 9 DoJ press release.
How it operates
A CISA Cybersecurity Advisory details the architecture, components and operation of Snake as well as mitigation techniques.
The Snake app uses software obfuscation, data encryption techniques and custom secure communication protocols to hide itself, and adapts to the environment into which it is deployed.
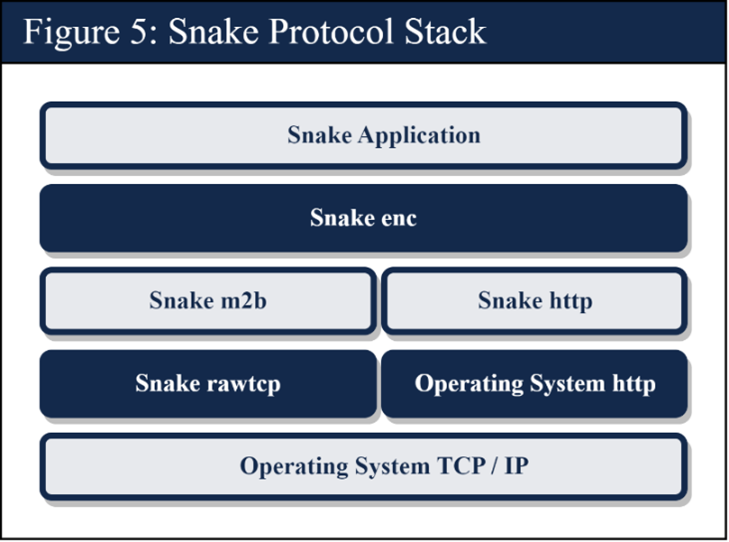
Snake’s targeting is purposeful and tactical in nature, leveraging infrastructure across all industries. If an infected system did not respond to Snake communications, FSB actors would strategically re-infect it within days. Globally, the FSB has used Snake to collect sensitive intelligence from high priority targets, such as government networks, research facilities, and journalists.
After stealing documents, Turla re-distributed them through a covert network of compromised compouters in the US and worldwide. Turla used the Snake network to route data exfiltrated from target systems through numerous relay nodes scattered around the world back to Turla operators in Russia.
How it was disrupted
An application for a search warrant filed by an FBI Special Agent to a US federal court in Brookly New York, which un-sealed the document to make it available online, details how the FBI proposed to conduct the MEDUSA counter-operation.
The FBI developed the capability to decrypt and decode Snake communications, which was described in court documents. With information gleaned from monitoring the Snake network and analyzing Snake malware, the FBI developed a tool named PERSEUS which establishes communication sessions with the Snake malware implant on a particular computer, and issues commands that causes the Snake implant to disable itself without affecting the host computer or legitimate applications on the computer.
Still a threat
Turla frequently deploys a “keylogger” with Snake that Turla can use to steal account authentication credentials, such as usernames and passwords, from legitimate users. Victims should be aware that Turla could use these stolen credentials to fraudulently re-access compromised computers and other accounts.
The operation to disable Snake did not patch any vulnerabilities or search for or remove any additional malware or hacking tools that hacking groups may have placed on victim. Although Operation MEDUSA disabled the Snake malware on compromised computers, victims should still take steps to protect themselves from harm.
Remaining vigilant
A joint cybersecurity advisory was issued by multiple US security agencies in collaboration with agencies from Australia, Canada, New Zealand, the United Kingdom (known as the Five Eyes), with detailed technical information about the Snake malware that will allow cybersecurity professionals to detect and remediate Snake malware infections on their networks.The Department of Justice strongly encourages network defenders to review the Joint Advisory for further guidance on detection and patching.
Further reading
Justice Department Announces Court-Authorized Disruption of Snake Malware Network Controlled by Russia’s Federal Security Service. Press release. May 9, 2023. US Department of Justice Office of Public Affairs
Hunting Russian Intelligence “Snake” Malware. Joint Cybersecurity Advisory. May 9, 2023. US Cybersecurity & Infrastructure Security Agency (CISA). Contains technical and structural details about Snake.
IN THE MATTER OF THE SEARCH OF INFORMATION ASSOCIATED WITH COMPUTERS CONSTITUTING THE SNAKE MALWARE NETWORK: AFFIDAVIT IN SUPPORT OF AN APPLICATION UNDER RULE 41 FOR A WARRANT TO SEARCH AND SEIZE. Application for search warrant against Turla and Snake (PDF). May 4, 2023. Docket No. 23-MJ-0428. US District Court of the Eastern District of New York
US Says It Dismantled Russia’s ‘Most Sophisticated’ Malware Network. Article. May 9, 2023. The New York Times (Paywall)
Why it matters
Using Snake, the FSB has victimized industries including media organizations, education and small businesses, as well as critical infrastructure sectors including government facilities, financial services, critical manufacturing, and communications. It demonstrates the size and scope of covert operations designed to compromise targets.
The DoJ said that although Snake has been the subject to several cybersecurity industry reports throughout its existence, Turla has applied numerous upgrades and revisions. Unless disrupted, the Snake implant persists on a compromised computer’s system indefinitely, typically undetected by the machine’s owner or authorized users.
Media industry stakeholders and creative professionals should monitor these cases with at least one eye, to understand how those threat platforms operate so they can justify cybersecurity initiatives that would reduce their own threat exposures – known or not.












