HUMAN Security (formerly White Ops), a company that specializes in detecting advertising fraud, published a detailed description of VASTFLUX, an automated scheme that infiltrated and spoofed in-app ad environments, reaching a peak volume of 12 billion ad bid requests per day; impacting nearly 11 million devices.
Now-defunct, VASTFLUX was apparently adapted from an earlier ad fraud scheme first reported in 2020. The operators that ran the VASTFLUX operation had an intimate understanding of the digital advertising ecosystem, evaded ad verification tags and deployed code that prevented its detection. The name VASTFLUX is derived from the concept of “fast flux”, an evasion technique used by cybercriminals, and VAST, the Digital Video Ad Serving Template, a standard of the Interactive Advertising Bureau (IAB).
Ads that run within apps generally run in restricted environments that pass less information to verification providers than ads that run on pages visited within a web browser. VASTFLUX exploited this gap in hope that it would take longer for the scheme to be detected and shut down.
How it worked
The VASTFLUX operation targeted more than 1,700 apps from 120 publishers. VASTFLUX code running in the app would bid for advertising from within the application, and upon winning an ad auction, would would request ads to be presented within the app. While the device user (end consumer) would see only one ad in their app, VASTFLUX would stack many as 25 video ads upon one another – and be paid for all of them.
Multi-step process
First, apps targeted by VASTFLUX made requests to the app’s primary supply-side partner (SSP) network for a banner ad to be displayed within the app, triggering a bidding process by demand-side partners (DSPs).
VASTFLUX-connected apps would then trigger the purchasing server to place a static banner image in the slot and inject several scripts. Next, the injected scripts discern the ad configuration, including the banner ad and other parameters that are delivered to the app in pieces (and thereby, are obfuscated) and then re-assembled into a URL in the VAST format.
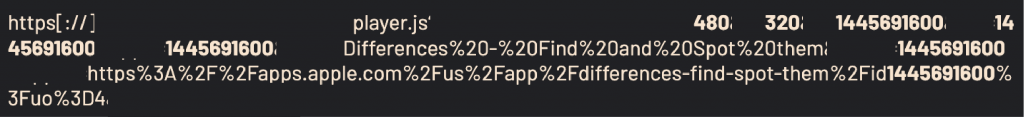
The reassembled URL includes the spoofed publisher ID, the geography and language setting, the spoofed app ID, and the poofed screen resolution.
The third step is to load a playlist of video ads, each with its own URL and tracking code. Configuration instructions received from the command-and-control server would adjust the tracking URLs of the VAST players to interfere with tracking.
The article goes on to specify best practices to reduce the likelihood that an advertiser fall victim to this attack. Platforms should ensure the full suite of IAB Tech Lab supply chain transparency standards is enforced: app-ads.txt to identify who is allowed to sell inventory; sellers.json to reveal seller identities and SupplyChain Object to reveal and validate authorization to sell for all intermediaries.
Read the full article and analysis: Traffic Signals: The VASTFLUX Takedown. HUMAN Security, January 19, 2023
Why it matters
Because the advertising came from legitimate sources, and when clicked, the ads took consumers to legitimate destinations, the consumer wasn’t really the one who was defrauded – although one could argue that they were taken to the ad’s destination under false pretenses.
Victimized consumers would experience short battery life, since video ads consume more power. They also would experience lags in performance, high data usage, and apps crashing. Devices could activate at unexpected times as fraudulently-delivered ads execute.
The damage really was inflicted on the advertising industry and upon the advertisers, whose payments-per-click padded the pockets of the VASTFLUX operators.












