Active since 2021, a network of malicious YouTube accounts has distributed thousands of malicious videos that serve as engagement mechanisms while those accounts distribute malware to trusting viewers, says a report by Check Point Research. Revenue from malware and ransomware are part of the business model for many piracy operations.
Ghost networks operate as a service, manipulating platform engagement mechanisms to lead users to believe these malicious activities are benign, and enable large-scale malware distribution. These have emerged as a distribution alternative to phishing emails and malicious Google Ad campaigns that serve malware to users who click through those campaigns.
A user who accesses malicious videos in this YouTube ghost network will see landing pages that display lots of ‘likes’ and encouraging comments, furthering trust. The report notes that the ‘Game Hacks/Cheats’ and ‘Software Cracks/Piracy’ categories attract large numbers of victims ongoing.
How it works
The majority of the YouTube ghost network consists of compromised YouTube accounts, which are assigned specific operational roles.
The three primary roles are Video accounts which contain videos and links to malicious software, Post accounts, which publish messages and posts that share download links and access credentials; and Interact accounts which post positive comments, likes and endorsements that foster trust.
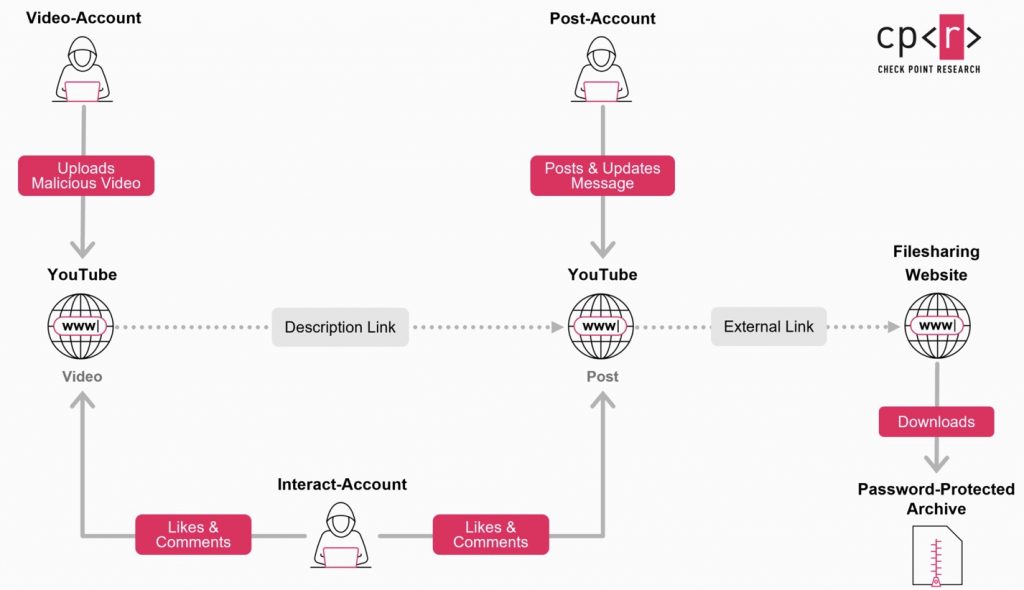
This role-based structure enables stealthy distribution, as banned accounts can be rapidly replaced without disrupting the overall operation.
Sources and methods
The external links found on these YouTube video landing pages typically redirect users to file-sharing services such as MediaFire, Dropbox, or Google Drive, or to phishing pages hosted on platforms like Google Sites, Blogspot, or Telegraph, says Check Point Research. These pages contain further links to download the malicious software. Shortened URLs are used to hide the true destination of the external link.
Check Point Research has been monitoring the YouTube Ghost Network for approximately a year and has identified multiple malware families, primarily infostealers. Until the disruption of Lumma between March and May 2025, Lumma was the most frequently distributed malware. Following that disruption, threat actors shifted to distributing Rhadamanthys as the preferred infostealer.
Earlier report
Check Point Research had previously published a detailed report describing ghost networks in 2024 as the category was emerging, with Stargazers Ghost Network as an example. Stargazers operates on GitHub, which gives it the illusion of being trustworthy.
Why it matters
Check Point Research observes that threat actors continuously adapt their tactics to discover new and effective methods for malware distribution. While email remains one of the most prominent infection vectors, its effectiveness has diminished due to widespread deployment of security solutions and increased user awareness. Consequently, attackers have sought alternative avenues, including malicious ad campaigns and ghost networks.
Further reading
Dissecting YouTube’s malware distribution network. Article. October 23, 2025. by Antonis Terefos (@tera0017). Check Point Research
Stargazers Ghost Network. Article. July 24, 2024. by Antonis Terefos (@Tera0017). Check Point Research










